BetterCAP is a powerful and versatile network tool used for network penetration testing, monitoring, and manipulation.
It provides a wide range of capabilities for analyzing and interacting with network traffic.
One of its distinctive features is the concept of “caplets.”
Table of Contents
Caplets in BetterCAP are small, reusable scripts or modules written in the Ruby programming language.
They allow you to extend and customize the functionality without modifying its core code.
Caplets are used to automate various tasks, perform specific attacks or manipulations, and enhance the tool’s overall capabilities.
They are essentially plugins or extensions that can be loaded to add specific functionalities.
BetterCAP manifests itself as a 'Swiss Army knife' when switched on to WiFi, Bluetooth Low Energy, wireless HID hijacking, and reconnaissance of IPv4 and IPv6 networks, along with MITM attacks. Its multifaceted nature brings to the fore a host of utilities, making it a highly sought-after tool in the relevant industries.

What is BetterCAP?
BetterCAP is a powerful security tool developed to audit the security of wireless networks.
It offers the ability to sniff network packets and supports various types of attacks and scanning activities like DNS spoofing, man-in-the-middle (MiTM) attacks, ARP spoofing, and other network intrusion techniques.
Main Features
- WiFi network scanning, de-authentication attack, clientless PMKID association attack, and automatic WPA/WPA2 client handshake capture.
- Bluetooth Low Energy devices scanning, characteristics enumeration, reading, and writing.
- 2.4 GHz wireless devices scanning and MouseJacking attacks with over-the-air HID frames injection (with DuckyScript support).
- Passive and active IP network hosts probing and recon.
- ARP, DNS, DHCPv6, and NDP spoofers for MITM attacks on IPv4 and IPv6-based networks.
- Proxies at packet level, TCP level, and HTTP/HTTPS application level are fully scriptable with easy-to-implement javascript plugins.
- A powerful network sniffer for credentials harvesting which can also be used as a network protocol fuzzer.
- A very fast port scanner.
- A powerful REST API with support for asynchronous events notification on web socket to orchestrate your attacks easily.
- An easy-to-use web user interface.
- More!
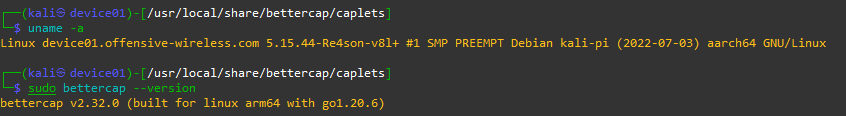
1. Preparing the Raspberry Pi
The preliminary step towards BetterCAP installation is ensuring your Raspberry Pi is up-to-date. By keeping your OS packages current, you create an optimal environment for BetterCAP to function at its best. Start the process with this terminal command:
sudo apt-get update && sudo apt-get -y upgradeActivate Bluetooth on RPI4
kali@kali:~$ sudo systemctl enable --now hciuart.service
kali@kali:~$ sudo systemctl enable --now bluetooth.service2. Install dependencies
- build-essential
- libpcap-dev
- libusb-1.0-0-dev (required by the HID module)
- libnetfilter-queue-dev (on Linux only, required by the packet.proxy module)
sudo apt updatesudo apt install golang git build-essential libpcap-dev libusb-1.0-0-dev libnetfilter-queue-dev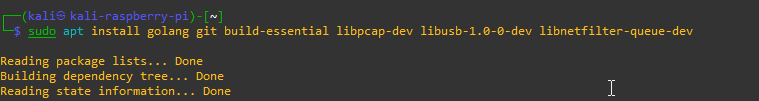
3. How to install Bettercap
First, we will install it from Git Hub, and after that all necessary dependencies.
sudo apt install bettercap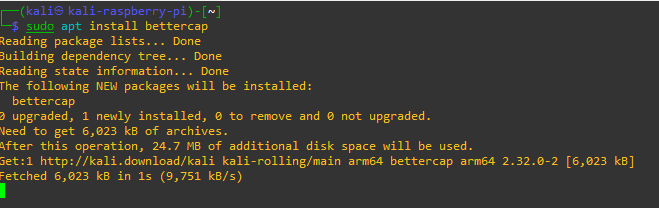
Compile from Source
go get github.com/bettercap/bettercap
cd $GOPATH/src/github.com/bettercap/bettercapmake build
sudo make install4. Update Caplets
sudo apt-get install bettercap-caplets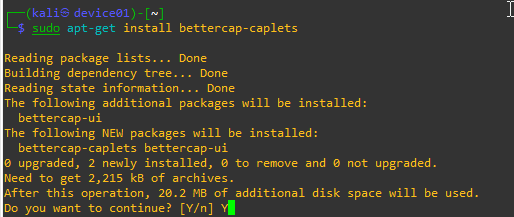
sudo bettercap -eval "caplets.update; q"5. BetterCap WebUI
sudo bettercap -eval "ui.update; q"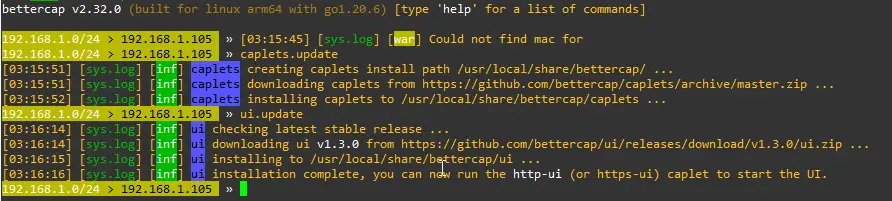
Configure Login
sudo vi /usr/local/share/bettercap/caplets/https-ui.cap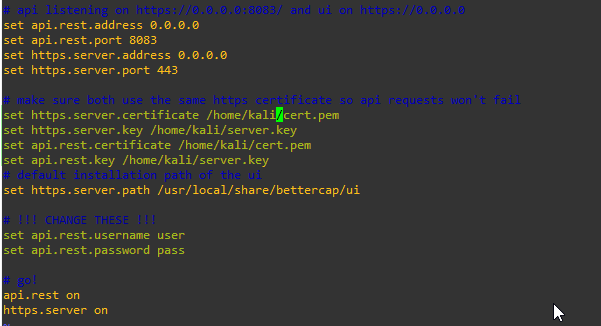
sudo bettercap -caplet https-uiGenerate a certificate for Web-Gui
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out bettercap-https.cert -sha256 -days 3650 -nodes -subj "/C=XX/ST=Oporto/L=Oporto/O=OffensiveWireless/OU=RFS/CN=kali"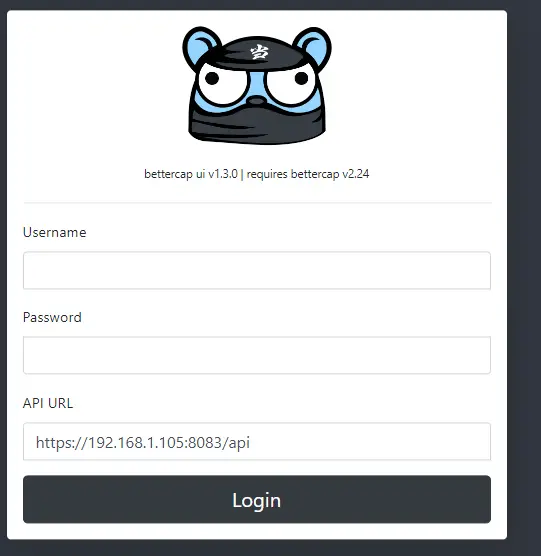
Before wrapping up, we would like to guide you to the official BetterCAP website. For your ease, we have revisited and expanded on some salient features in a more comprehensive manner:
Scanning, enumeration, reading and writing characteristics of Bluetooth low energy devices. Conducting reconnaissance and mitm attacks on ipv4 and ipv6 networks. Understanding proxies at packet level, tcp level, and application level(http,https). Capturing WPA/WPA2 client handshakes.
Bluetooth low energy devices scanning characteristics enumeration reading and writing.
ipv4 and ipv6 networks reconnaissance and mitm attacks.
proxies at packet level tcp level and http https application level
wpa/wpa2 client handshakes capturesudo bettercap --help
Usage of bettercap:
-autostart string
Comma separated list of modules to auto start. (default "events.stream")
-caplet string
Read commands from this file and execute them in the interactive session.
-caplets-path string
Specify an alternative base path for caplets.
-cpu-profile file
Write cpu profile file.
-debug
Print debug messages.
-env-file string
Load environment variables from this file if found, set to empty to disable environment persistence.
-eval string
Run one or more commands separated by ; in the interactive session, used to set variables via command line.
-gateway-override string
Use the provided IP address instead of the default gateway. If not specified or invalid, the default gateway will be used.
-iface string
Network interface to bind to, if empty the default interface will be auto selected.
-mem-profile file
Write memory profile to file.
-no-colors
Disable output color effects.
-no-history
Disable interactive session history file.
-pcap-buf-size int
PCAP buffer size, leave to 0 for the default value. (default -1)
-script string
Load a session script.
-silent
Suppress all logs which are not errors.
-version
Print the version and exit.




