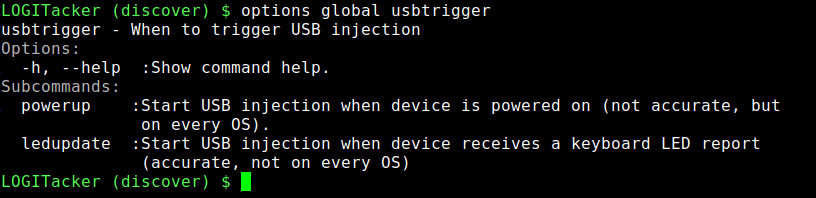
Learn how LOGITaker works and setup your own to attack near keyboards.
Table of Contents
Hardware nRF52840 radio dongle
- Nordic nRF52840 Dongle (pca10059)
- MakerDiary MDK Dongle
- MakerDiary MDK
- April Brother Dongle
Logitech Vulnerabilities
- MouseJack (plain injection)
- forced pairing
- CVE-2019-13052 (AES key sniffing from pairing)
- CVE-2019-13054 (injection with keys dumped via USB from presentation clickers)
- CVE-2019-13055 (injection with keys dumped via USB from Unifying devices)
LOGITacker Virtual USB devices
- USB CDC ACM
- USB mouse
- USB keyboard
- USB HID raw
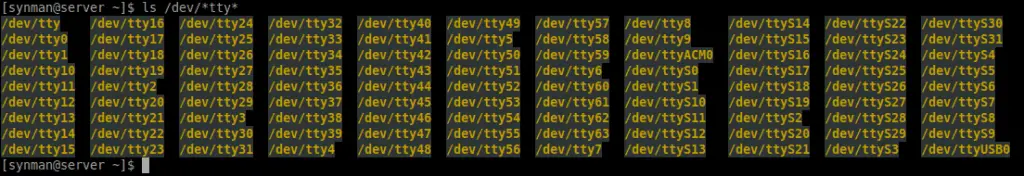
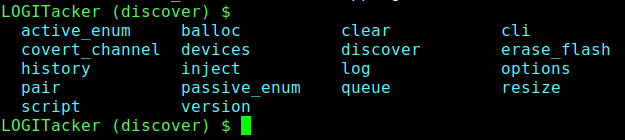
LOGITacker Options
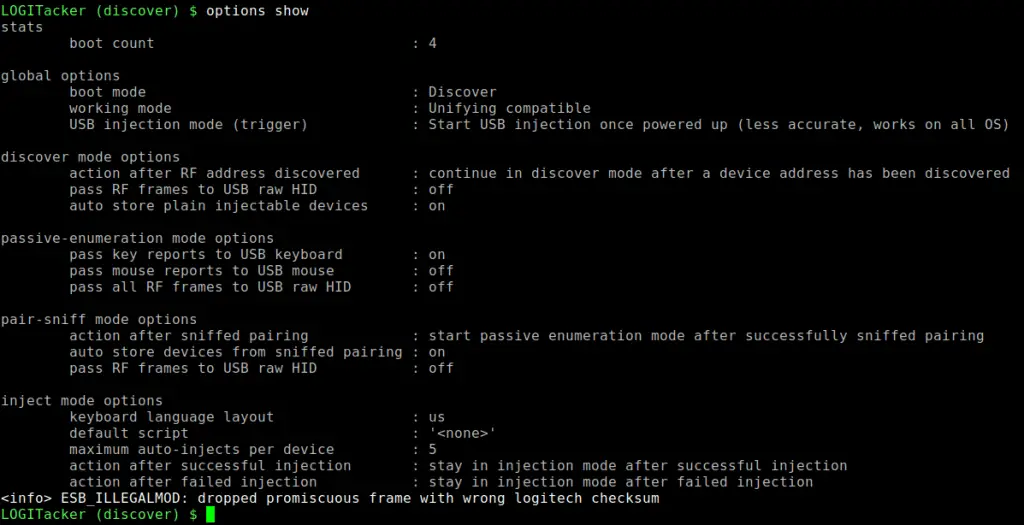
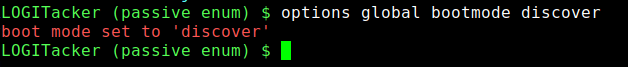
Boot Mode
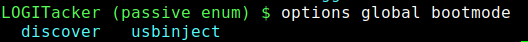
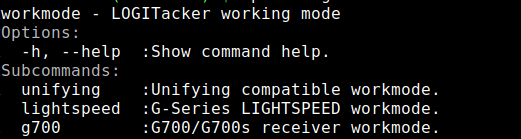
Working Mode
USB Injection