This article (Bluetooth Penetration Testing Fundamentals) attempts to give an overview of the technology, terms, and security that are built into Bluetooth.
I hope this will allow you to get started in hacking Bluetooth without getting bogged down by too much technical detail.
Before starting any hacking tutorials, you need to understand the technology.
Table of Contents
To do that, you need to know the terms, and what they mean, as well as how they are used in the context of Bluetooth, which is the topic of this tutorial.
The first thing to understand is that Bluetooth is an open standard that allows devices to communicate with each other over short distances (usually around 10 meters).
There are several communication protocols built on top of this basic idea, but one of the most well-known is the A2DP (application data profile) standard. This allows for the streaming of audio over a short distance, similar to Wi-Fi or USB.
If you don’t know how Bluetooth works, it’s hard to hack it. You need to understand key terms like the modes, encryption types, and security settings that allow us to adequately prepare for hacks.
In this short article, we’ll simplify some of these concepts and provide some examples of how to use them in our testing.

Hardware
This is the protocol that enables devices to connect to each other wirelessly. It uses the same radio transceiver and antenna as Wi-Fi.
Bluetooth can be used for a variety of applications, ranging from a simple pairing of two devices (like a computer and its keyboard) to voice-over IP for phone calls.
Each device also transmits information about its capabilities, which Bluetooth devices can use to detect another device. This gives you some basic information about the other device, including its name and what it is capable of doing or displaying.
It’s quite easy to pair any two devices over Bluetooth, although it takes some time if they’re not in close proximity (i.e., much longer when both devices are on different networks).
Types of Bluetooth
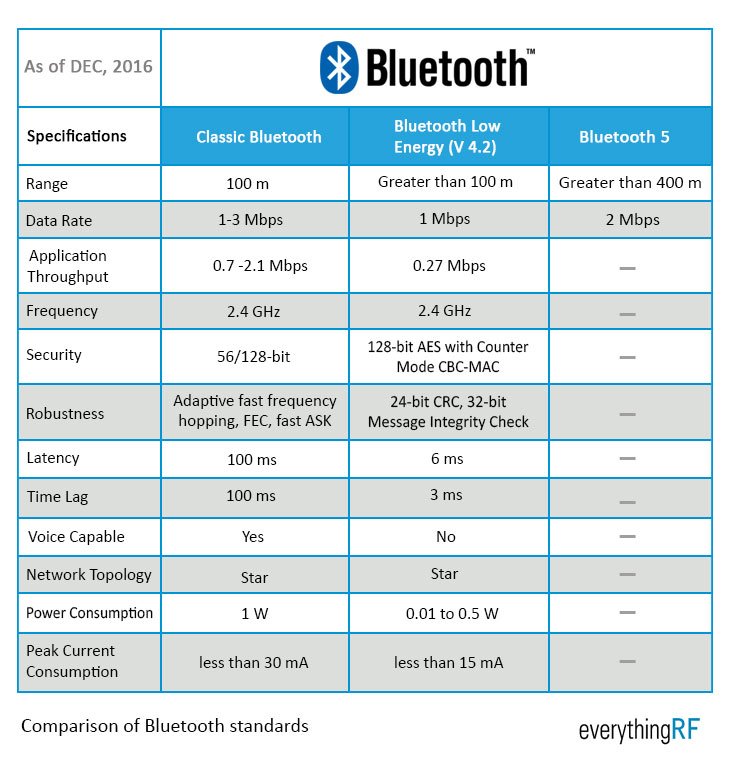
Classic
Classic Bluetooth has several advantages, including:
- Wide range: Classic Bluetooth has a range of up to 10 meters (33 feet), which is sufficient for most applications.
- High data rate: The maximum data transfer rate of Classic Bluetooth is 2.1 Mbps, which is sufficient for most applications.
- Wide compatibility: Classic Bluetooth is compatible with a wide range of devices.
Classic Bluetooth devices have high data throughput and high battery consumption.
79 channels of 1MHz with a clock of 625us
Sophisticated PHY Modulation
Low Energy
Low data throughput but a long battery lifetime.
40 channels of 2 MHz and use events spaced in multiples of 1.25ms.
Simple PHY Modulation
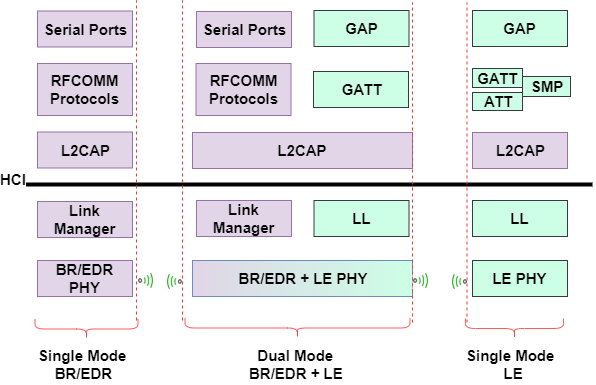
Pairing Process
Pairing is a process of making a Bluetooth device discoverable to other devices. This process can be verified by looking for its presence on the list of connected devices in the smartphone.
When a user pairs two devices, one is usually paired as an ‘access point’ and the other as an ‘attached peripheral’.
The remote device can then transform from being a Bluetooth EDR to a Bluetooth HCI device.
The term AAA (Acquiring Application Access) is commonly used for this process.
This not only allows two devices to exchange information via the connection but also creates identities within the connected devices by assigning a unique name (name). In this way, the users are immediately aware of who they are talking to or receiving data from.
Bluetooth Penetration Testing
Many Bluetooth devices have been compromised because the pre-shared key is often not secured.
When a device goes through pairing mode, both devices exchange a secret key and this lets them communicate for the first time.
This key is then used to authenticate between devices and encrypt their communications.
Someone with physical access to either the master or slave can reconfigure that device’s physical jumper pins and gain control over both devices. As long as one knows this pre-shared key
Bluetooth Penetration Testing tools
There are several different tools that can be used for Bluetooth penetration testing. Some of the most popular tools include:
- BlueZ: This is a Linux-based Bluetooth stack that provides several tools for scanning, probing, and interacting with Bluetooth devices.
- Bluesniff: This tool is used to capture and analyze Bluetooth traffic.
- Bluelog: This tool is used to log Bluetooth events.
- Bluepot: This is a Bluetooth honeypot that can be used to identify and capture Bluetooth attacks.
How to Bluejack a Bluetooth device
How to BlueSmacking a Bluetooth device





